Endpoint Security: Strategies to Protect Your Devices
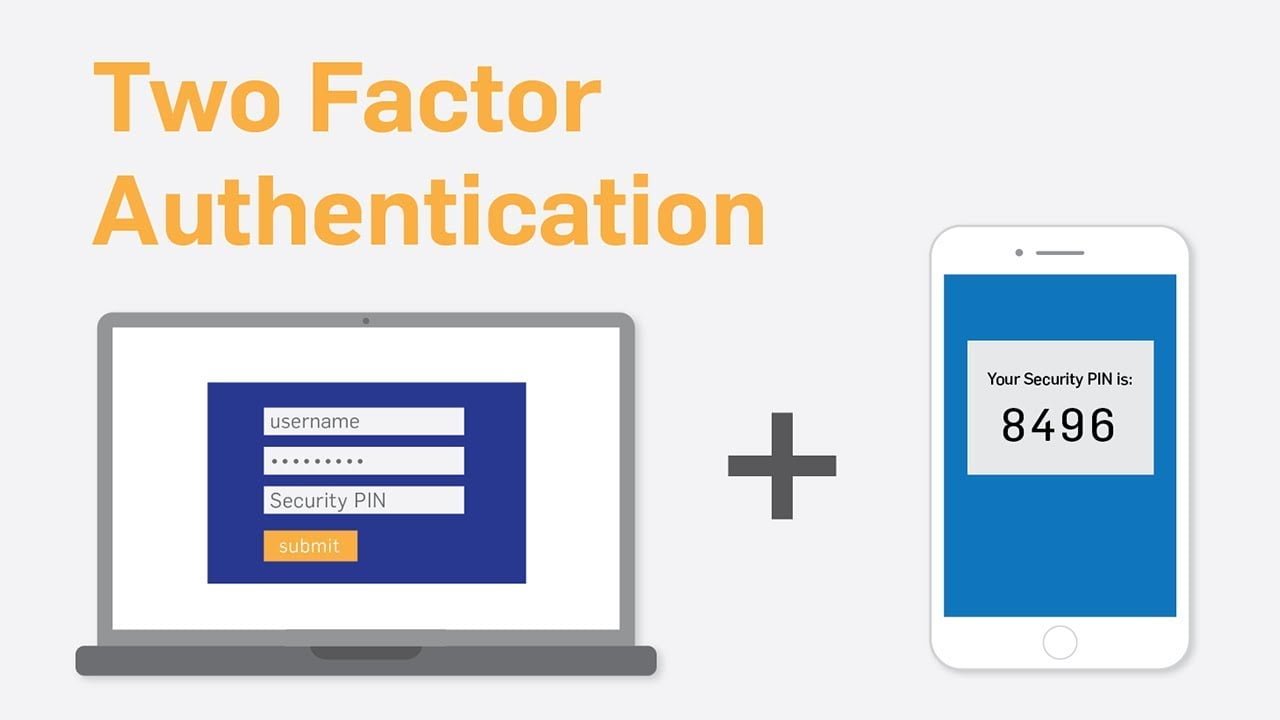
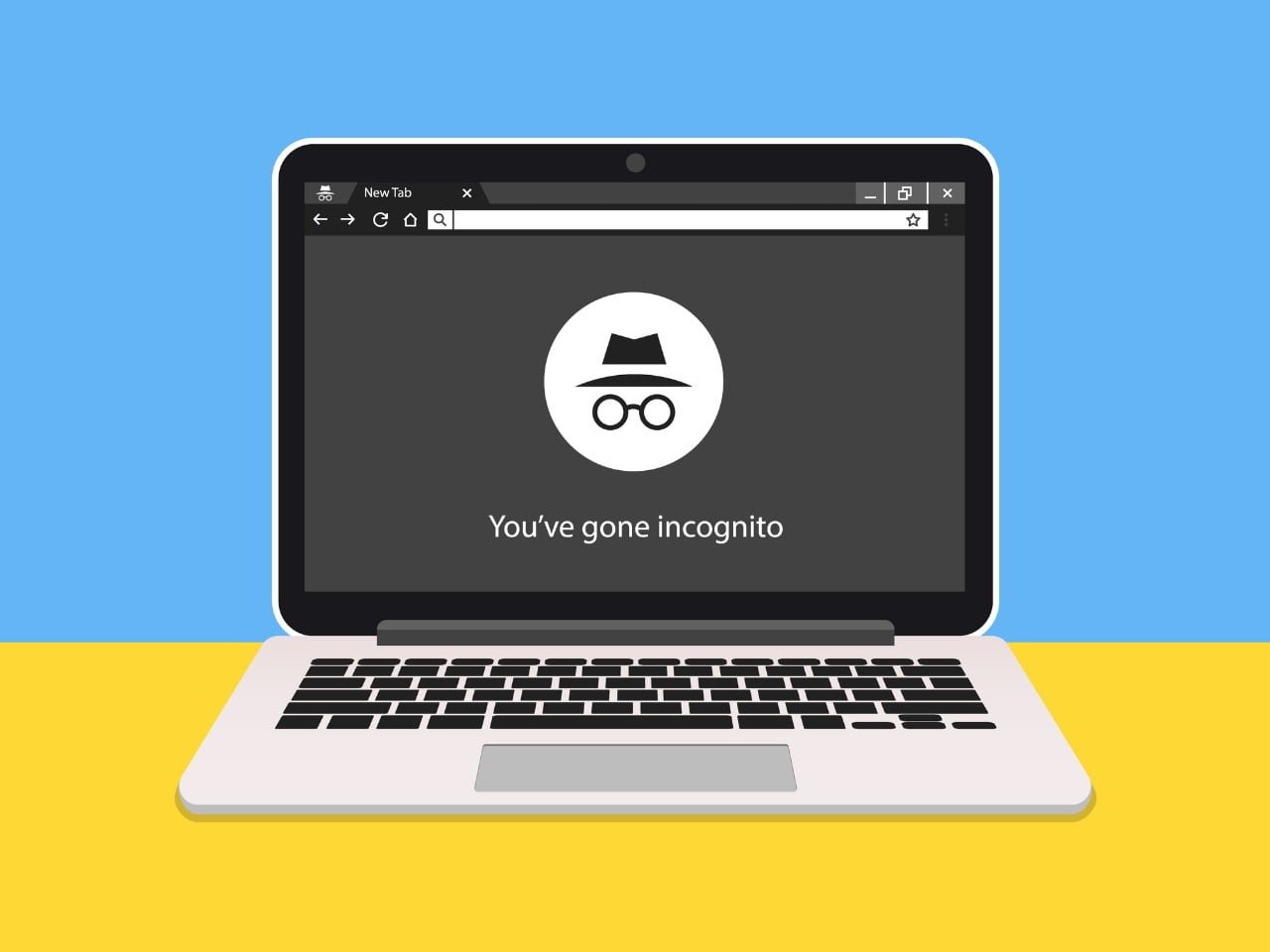
Introduction In today’s digital landscape, the security of our devices is of paramount importance. With the increasing number of cyber threats, it is crucial to implement effective endpoint security strategies to safeguard our devices and sensitive data. This blog post will provide you with valuable insights and practical tips to protect your devices from potential … Read more