Introduction
In today’s digital age, where cyber threats are on the rise, it is crucial to take every possible measure to protect our online accounts and sensitive information. One effective way to enhance security is by implementing two-factor authentication (2FA). In this article, we will discuss the importance and use of two-factor authentication and how it can significantly improve the safety of our online presence.
What is Two-Factor Authentication?
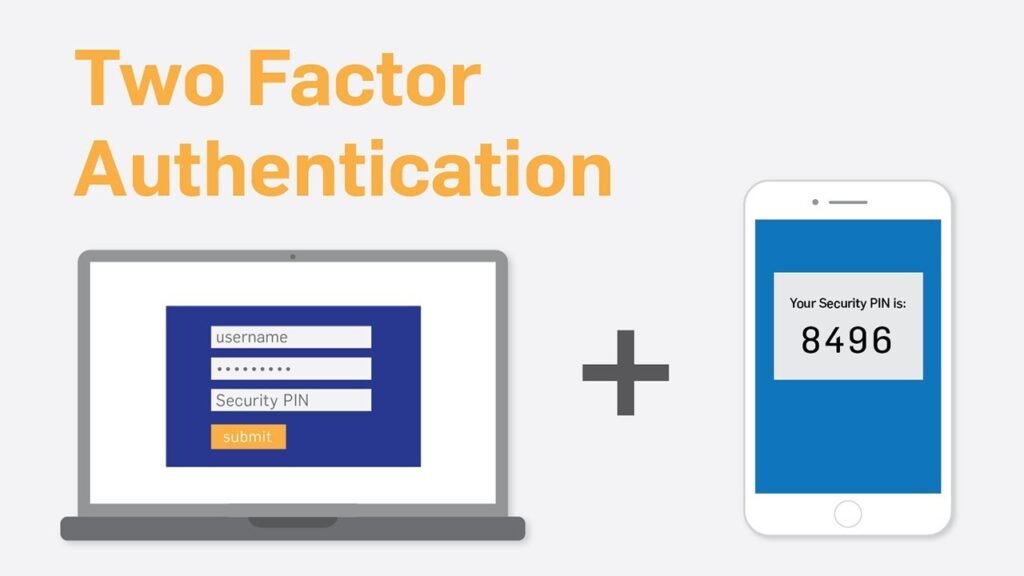
Two-factor authentication, also known as 2FA, is an additional layer of security that helps verify the identity of users when accessing online accounts. It adds an extra step to the traditional username and password login process by requiring users to provide a second piece of information, typically a unique code sent to their mobile device or generated by an authentication app.
The Importance of Two-Factor Authentication
1. Enhanced Security: 2FA provides an additional layer of security, making it significantly harder for unauthorized individuals to gain access to our accounts. Even if someone manages to obtain our password, they would still need the second factor to log in successfully.
2. Protection Against Password Theft: With the increasing number of data breaches and password leaks, it has become easier for cybercriminals to obtain user credentials. 2FA acts as a safeguard against password theft, as the second factor is often only accessible to the account owner.
3. Mitigation of Phishing Attacks: Phishing attacks, where attackers trick users into revealing their login credentials through fraudulent websites or emails, are a common threat. 2FA can help mitigate the impact of such attacks, as even if users unknowingly provide their password, the second factor would prevent unauthorized access.
4. Compliance with Regulatory Requirements: Many industries, such as finance and healthcare, are subject to strict regulations regarding data protection. Implementing two-factor authentication can help organizations meet these requirements and ensure the security of sensitive information.
How Two-Factor Authentication Works
The process of two-factor authentication typically involves the following steps:
- User enters their username and password on the login page.
- A unique code is sent to the user’s mobile device via SMS or generated by an authentication app.
- The user enters the code on the login page to complete the authentication process.
Alternatively, some services offer biometric factors, such as fingerprint or facial recognition, as the second factor for authentication.
Types of Two-Factor Authentication
There are several types of two-factor authentication methods available:
1. SMS-Based Authentication: This method involves receiving a unique code via SMS on the user’s mobile device. The user then enters the code to authenticate their login.
2. Authentication Apps: These apps generate time-based one-time passwords (TOTP) that users enter to verify their identity. Examples of popular authentication apps include Google Authenticator and Authy.
3. Hardware Tokens: Some organizations provide physical hardware tokens that generate unique codes for authentication. These tokens are often used in high-security environments.
4. Biometric Authentication: This method uses unique physical characteristics, such as fingerprints or facial features, to verify the user’s identity.
FAQs (Frequently Asked Questions)
- Q: Is Two-Factor Authentication (2FA) necessary if I have a strong password? A: While a strong password is crucial, 2FA provides an extra layer of security by requiring a second form of verification, making it significantly harder for unauthorized individuals to access your accounts, even if they obtain your password.
- Q: Can I use Two-Factor Authentication (2FA) for all my online accounts? A: Many online services and platforms support 2FA, including social media, email providers, and financial institutions. It’s highly recommended to enable 2FA wherever possible to enhance the security of your accounts.
- Q: What happens if I lose access to the device used for Two-Factor Authentication (2FA)? A: If you lose access to your mobile device or authentication app, some services offer backup methods such as backup codes or alternative contact methods to regain access to your account. It’s essential to set up these backup options when enabling 2FA.
- Q: Can Two-Factor Authentication (2FA) be bypassed by hackers? A: While no security measure is entirely foolproof, 2FA significantly reduces the risk of unauthorized access. However, some sophisticated attacks may attempt to bypass 2FA, highlighting the importance of staying vigilant and using additional security measures.
- Q: Is Two-Factor Authentication (2FA) complicated to set up and use? A: Setting up 2FA is typically straightforward, and many services provide step-by-step instructions for enabling it on your account. Once set up, the authentication process usually involves entering a code sent to your mobile device or generated by an app, which adds only a few seconds to the login process for enhanced security.
Conclusion
Two-factor authentication is an essential tool in today’s digital landscape, offering enhanced security and protection against unauthorized access. By implementing this additional layer of verification, we can significantly reduce the risk of cyber threats and safeguard our online accounts and sensitive information.