Industrial Control Systems (ICS) are the invisible backbone of our modern world. From power grids to water treatment facilities, manufacturing plants to transportation networks, these systems control the critical infrastructure that keeps society functioning. Yet, 87% of industrial organizations have experienced at least one cyber incident in the past year, with attacks growing more sophisticated and devastating.
If you’re responsible for ICS security, you’re literally holding the keys to critical infrastructure. The stakes couldn’t be higher, and traditional IT security approaches simply don’t cut it in operational technology (OT) environments.
The Alarming Reality of ICS Cyber Threats
The threat landscape for Industrial Control Systems has evolved dramatically. We’re not just dealing with script kiddies anymore – we’re facing nation-state actors, sophisticated criminal organizations, and insider threats that understand the unique vulnerabilities of industrial environments.
Recent Attack Trends That Should Keep You Awake
The Colonial Pipeline Attack (2021) shut down the largest fuel pipeline in the US for six days, causing nationwide fuel shortages and costing billions in economic damage. The attackers didn’t even directly target the operational systems – they compromised IT networks, but operators shut down OT systems as a precaution.
The Ukraine Power Grid Attacks (2015, 2016) demonstrated how attackers could remotely manipulate industrial control systems to cause widespread blackouts, affecting hundreds of thousands of people.
These aren’t isolated incidents. Dragos Intelligence reports a 25% increase in ICS-specific malware families, with threat groups specifically developing tools to target industrial environments.
Understanding the Unique ICS Threat Landscape
Industrial Control Systems face a perfect storm of security challenges that don’t exist in traditional IT environments:
Legacy System Vulnerabilities
Most ICS deployments include systems that were designed 20-30 years ago when air-gapping was considered sufficient security. These systems often run on:
- Unpatched operating systems (Windows XP, Windows 2000)
- Proprietary protocols with no built-in security
- Hard-coded credentials that can’t be changed
- Unsupported hardware with known vulnerabilities
The Convergence Challenge
Modern industrial facilities increasingly connect OT networks to IT systems for business intelligence, remote monitoring, and efficiency optimization. This convergence creates new attack vectors:
Lateral Movement Opportunities: Attackers who compromise IT networks can pivot to OT systems Remote Access Vulnerabilities: VPN connections and remote maintenance tools create entry points Cloud Integration Risks: Industrial IoT devices often communicate with cloud platforms, expanding the attack surface
Critical ICS Network Security Risks: A Deep Dive
Let’s examine the most dangerous threats facing industrial control systems today:
1. Protocol-Specific Attacks
Industrial protocols like Modbus, DNP3, and EtherNet/IP were designed for reliability and speed, not security. Attackers exploit these protocol weaknesses:
Modbus Vulnerabilities:
- No authentication mechanisms
- Commands sent in clear text
- Easy to spoof device communications
DNP3 Exploitation:
- Weak challenge-response authentication
- Susceptible to man-in-the-middle attacks
- Function code manipulation possibilities
EtherNet/IP Risks:
- Uses standard TCP/IP but lacks encryption
- Vulnerable to network scanning and enumeration
- Susceptible to denial-of-service attacks
2. Human Machine Interface (HMI) Compromises
HMI systems are often the weakest link in ICS security:
- Default credentials on HMI software
- Unencrypted communications between HMI and PLCs
- Web-based interfaces with standard web vulnerabilities
- USB ports that can introduce malware
3. Engineering Workstation Attacks
Engineering workstations have privileged access to configure and program industrial systems:
- Often connected to both corporate and control networks
- Run specialized software with known vulnerabilities
- Users frequently have elevated privileges
- May contain configuration files and network diagrams
4. Wireless and Remote Access Vulnerabilities
Modern industrial facilities increasingly use wireless technologies:
Wireless Sensor Networks: Often deployed with default configurations Cellular Modems: Used for remote monitoring but poorly secured Satellite Communications: Vulnerable to interception and jamming Remote Maintenance Tools: Create persistent backdoors if compromised
Advanced Persistent Threats Targeting ICS
APT groups have developed sophisticated techniques specifically for industrial environments:
TRITON/TRISIS Malware
Specifically designed to target Schneider Electric Triconex safety systems. This malware could disable safety controls, potentially causing physical damage or harm.
INDUSTROYER/CrashOverride
The first malware designed to directly target industrial control systems, used in the Ukraine power grid attacks. It can control switches and breakers in electrical substations.
Havex RAT
Specifically targets ICS/SCADA systems through infected software installers and watering hole attacks on industrial websites.
ICS Network Segmentation: Your First Line of Defense
Proper network segmentation is crucial for ICS security. Here’s the gold standard architecture:
Purdue Model Implementation
Level 0 (Field Devices): Sensors, actuators, drives Level 1 (Control Systems): PLCs, DCS controllers, RTUs Level 2 (Supervision): HMIs, engineering workstations Level 3 (Operations): Manufacturing execution systems Level 4 (Business): ERP, corporate networks
Each level should have appropriate security controls and limited communication between levels.
Zone and Conduit Strategy
Create security zones based on:
- Risk assessment results
- Functional requirements
- Regulatory compliance needs
Implement conduits (secure communication channels) between zones with:
- Firewalls configured for industrial protocols
- Data loss prevention systems
- Protocol validation capabilities
Industrial Firewall Configuration: Beyond Traditional IT
Standard IT firewalls don’t understand industrial protocols. You need specialized industrial firewalls that can:
Deep Packet Inspection for Industrial Protocols
- Validate Modbus function codes
- Monitor DNP3 message integrity
- Detect abnormal EtherNet/IP communications
Application Layer Filtering
- Block unauthorized HMI commands
- Prevent unauthorized configuration changes
- Monitor for suspicious automation behavior
Protocol Whitelisting
Instead of blacklisting known bad traffic, whitelist only authorized:
- Device communications
- Function codes
- Data ranges
- Timing patterns
Asset Discovery and Inventory: Know What You’re Protecting
You can’t secure what you don’t know exists. Industrial environments often have:
Shadow IT/OT Devices
- Maintenance laptops connected temporarily
- Unauthorized wireless access points
- Personal devices on industrial networks
- Forgotten test equipment
Legacy Device Discovery Techniques
Passive Network Monitoring: Use tools like Nozomi Networks or Claroty to identify devices without disrupting operations
Active Scanning: Carefully scan networks during maintenance windows using tools like:
- Nmap with industrial scripts
- Redpoint for ICS-specific discovery
- Shodan for internet-exposed industrial devices
Monitoring and Detection: Seeing the Invisible
Traditional antivirus and SIEM solutions don’t work well in industrial environments. You need specialized monitoring:
Behavioral Analytics for Industrial Systems
Monitor for:
- Unusual communication patterns between devices
- Unauthorized configuration changes to PLCs
- Abnormal process behaviors that could indicate manipulation
- Time-based anomalies in automation sequences
Industrial Protocol Monitoring
Deploy monitoring solutions that understand:
- Normal vs. abnormal Modbus traffic
- Expected DNP3 message flows
- Typical EtherNet/IP communication patterns
- SCADA polling cycles and responses
Insider Threat Detection in Industrial Environments
Insider threats are particularly dangerous in industrial settings:
Privileged User Monitoring
- Track all engineering workstation activities
- Monitor PLC programming changes
- Log HMI configuration modifications
- Alert on unusual maintenance activities
Contractor and Vendor Management
- Implement zero-trust access for third parties
- Monitor vendor remote access sessions
- Require multi-factor authentication
- Time-limit vendor access credentials
Incident Response for Industrial Control Systems
ICS incident response differs significantly from IT incident response:
Safety First Approach
- Prioritize personnel safety over system availability
- Coordinate with safety personnel before taking action
- Understand the physical impact of cybersecurity decisions
- Have manual override procedures ready
Evidence Preservation Challenges
- Industrial systems can’t be easily shut down for forensics
- Live memory analysis may be the only option
- Network captures must not disrupt control communications
- Consider regulatory requirements for evidence handling
Regulatory Compliance and Standards
Different industries have specific ICS security requirements:
NERC CIP (Electric Utilities)
- Asset identification and categorization
- Cyber security controls for critical assets
- Personnel training and background checks
- Incident reporting requirements
ISA/IEC 62443 (Industrial Automation)
- Security lifecycle requirements
- Zone and conduit models
- Security level definitions
- Risk assessment methodologies
NIST Cybersecurity Framework
- Identify, Protect, Detect, Respond, Recover
- Specifically adapted for industrial environments
- Provides flexible implementation guidance
Advanced ICS Security Techniques
Honeypots and Deception Technology
Deploy fake industrial devices to detect attackers:
- Virtual PLCs that look real but monitor access attempts
- Fake HMI systems with tempting but false data
- Decoy engineering workstations with monitoring capabilities
Machine Learning for Anomaly Detection
- Train models on normal industrial process behavior
- Detect subtle deviations that could indicate attacks
- Reduce false positives through industrial context awareness
Zero Trust Architecture for OT
- Verify every device and user before granting access
- Continuously monitor and validate trust levels
- Implement micro-segmentation within industrial networks
Future Threats and Preparation Strategies
The ICS threat landscape continues to evolve:
AI-Powered Attacks
Attackers will use artificial intelligence to:
- Learn normal industrial process behaviors
- Craft more sophisticated attacks
- Automate lateral movement through industrial networks
Supply Chain Compromises
- Malware embedded in industrial software updates
- Compromised industrial devices from manufacturers
- Third-party service provider compromises
5G and Edge Computing Risks
- New attack surfaces in industrial 5G implementations
- Edge computing devices with poor security
- Increased connectivity creating more entry points
Building Your ICS Security Program
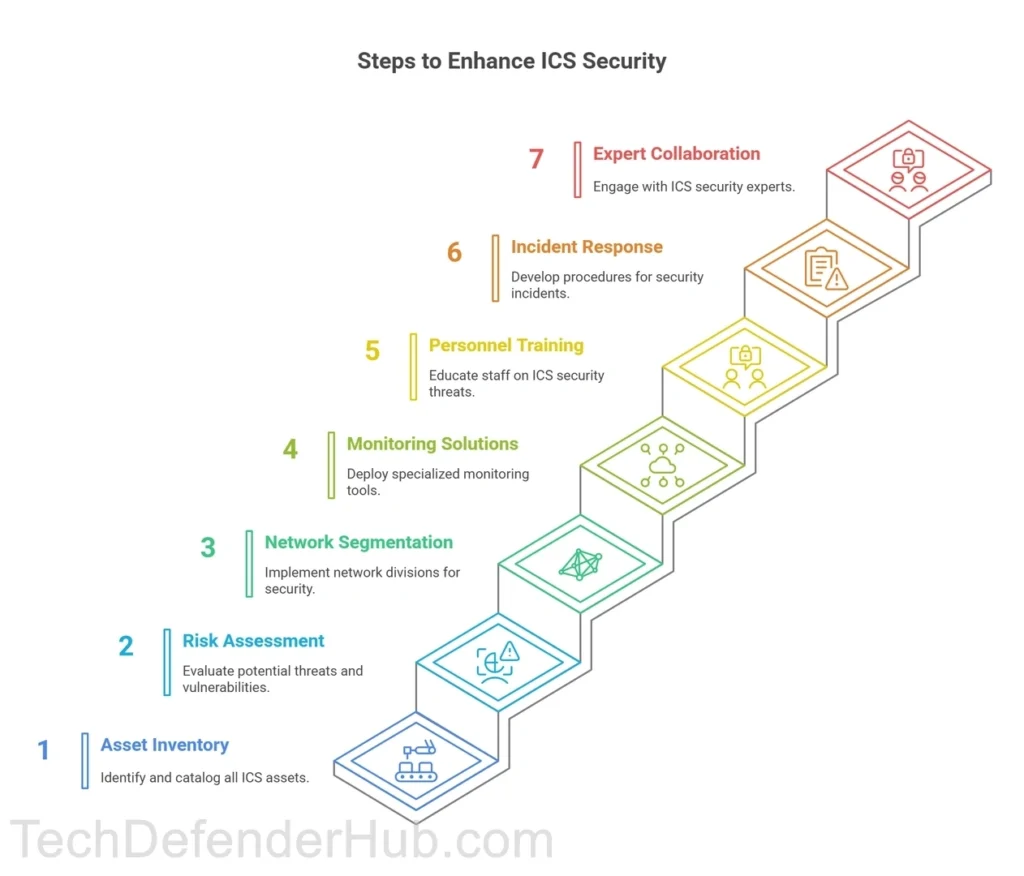
Start with these critical steps:
- Conduct a comprehensive asset inventory
- Perform risk assessments specific to your industrial processes
- Implement network segmentation based on the Purdue model
- Deploy industrial-specific monitoring solutions
- Train personnel on ICS-specific security threats
- Develop incident response procedures for industrial environments
- Establish relationships with ICS security experts and vendors
The Bottom Line: ICS Security is National Security
Industrial Control System security isn’t just about protecting your organization – it’s about protecting critical infrastructure that society depends on. The convergence of IT and OT networks, sophisticated threat actors, and the increasing connectivity of industrial systems create a perfect storm of security challenges.
The good news? With proper planning, specialized tools, and a deep understanding of industrial environments, you can significantly reduce your risk. The key is recognizing that ICS security requires specialized knowledge, tools, and approaches that differ from traditional IT security.
Remember: in industrial environments, confidentiality, integrity, and availability have different priorities than in IT systems. Safety always comes first, followed by availability, then integrity, and finally confidentiality. This fundamental difference drives every security decision you make.
Your industrial control systems are too important to secure with generic approaches. Invest in specialized ICS security solutions, training, and expertise. The critical infrastructure of tomorrow depends on the security decisions you make today.
What ICS security challenges are you facing in your industrial environment? Have you implemented any of these advanced techniques? The industrial cybersecurity community grows stronger when we share knowledge and experiences.

