Introduction
In 2025, mobile application security has become a cornerstone of digital safety. With the explosion of mobile apps for everything from banking to entertainment, the threat of malware attacks has reached unprecedented levels. Protecting against these risks requires both innovation and vigilance.
Evolution of Mobile Malware
Early Stages of Mobile Malware
Mobile malware was once rudimentary, primarily targeting SMS scams and basic data theft. These early threats were limited in scope but highlighted the vulnerabilities in mobile systems.
Rising Sophistication in Malware Attacks
Over the years, malware has evolved into highly complex forms. Attackers now deploy advanced techniques like zero-day exploits, targeting vulnerabilities before they’re patched.
Key Incidents Shaping Current Security Measures
Notable breaches, such as the Pegasus spyware scandal, have reshaped the approach to mobile security, driving investment in advanced defense mechanisms.
Current Mobile Security Landscape
Overview of 2025’s Mobile App Ecosystem
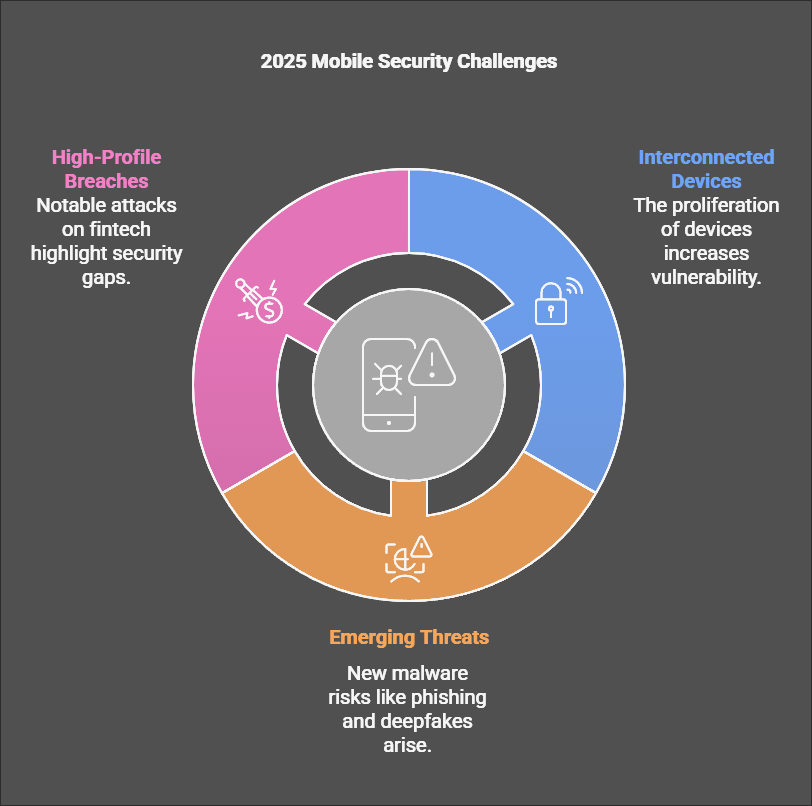
The app landscape is now more interconnected, with billions of devices operating across global networks. While this brings convenience, it also expands the attack surface.
Emerging Threats in Mobile Application Security
From phishing apps to deepfake-driven fraud, 2025 presents a diverse range of malware risks.
Case Studies of Recent Malware Breaches
High-profile breaches, such as those targeting fintech apps, underscore the need for improved defense strategies.
Common Types of Mobile Malware
Trojans and Spyware
These malicious programs disguise themselves as legitimate apps, stealing sensitive data like login credentials and financial details.
Ransomware on Mobile Platforms
Ransomware is no longer confined to PCs. Mobile users face demands to pay attackers to regain access to their locked devices.
Adware and Click Fraud
These less-severe forms of malware generate fraudulent ad clicks, affecting both users and advertisers.
Challenges in Mobile Application Security
Balancing a seamless user experience with robust security measures remains a challenge. Furthermore, app developers face mounting complexity in ensuring their code is impervious to attacks. Most importantly, many users remain unaware of the basic practices to avoid malware.
The Role of AI and Machine Learning
AI has become indispensable in malware detection. Machine learning algorithms analyze app behavior to identify anomalies indicative of malware. These technologies will continue to revolutionize how we defend against threats.
Best Practices for Mobile App Developers
- Secure Coding Practices: Following frameworks like OWASP ensures apps are built securely from the ground up.
- Regular Vulnerability Assessments: Frequent testing uncovers potential flaws before attackers do.
- Security Updates and Patches: Timely updates mitigate known vulnerabilities, keeping users safe.
Best Practices for End Users
Users play a vital role in malware prevention. Recognizing suspicious app behavior, managing app permissions, and keeping devices updated are essential steps to stay secure.
Role of Governments and Organizations
Global regulations have become stricter, requiring app developers to adhere to rigorous security standards. Meanwhile, public-private partnerships aim to educate users and tackle threats collaboratively.
Advanced Security Solutions
Endpoint Detection and Response (EDR) Systems
These systems monitor and respond to threats in real time, minimizing damage.
Mobile Threat Defense (MTD) Solutions
MTD tools provide comprehensive protection by analyzing network and app behavior.
Role of Blockchain in Mobile App Security
Blockchain ensures data integrity and enhances app security by decentralizing trust.
Trends in Mobile Malware Protection
Biometric Authentication as a Security Layer
Advanced biometrics like facial recognition and fingerprint scanning add an extra layer of protection.
Evolution of App Store Vetting Processes
App stores are increasingly leveraging AI to detect and eliminate malware-laden apps before they reach users.
Growth of Zero-Trust Architecture
Zero-trust frameworks ensure every interaction is verified, reducing exposure to threats.
Preparing for Future Threats
Anticipating future challenges requires a mix of innovation and preparation. Proactive strategies, such as predictive threat modeling, will be vital in defending against evolving malware.
Conclusion
Mobile application security in 2025 demands a proactive and multifaceted approach. As threats become more sophisticated, so must our defenses. By embracing AI-driven tools, adopting best practices, and fostering global collaboration, we can stay one step ahead.
FAQs
Mobile malware includes malicious software that infiltrates devices to steal data or cause harm, often resulting in financial losses or privacy breaches.
Secure coding, regular vulnerability assessments, and prompt updates are key strategies.
AI detects unusual app behavior, predicts threats, and enables rapid responses to attacks.
Unusual battery drainage, frequent crashes, and unauthorized data usage are common indicators.
Yes, stringent regulations enforce accountability and push developers toward higher security standards

